Crypto
New York’s Proof-Of-Work Ban Violates Bitcoin Miners’ Right To Free Speech
Published
2 years agoon

This is an opinion editorial by Aaron Daniel, an appellate attorney and author of The Bitcoin Brief legal research newsletter.
Introduction
New York’s legislative assembly passed Bill No. A07389 on June 2, 2022, “establishing a moratorium on cryptocurrency mining operations that use proof-of-work authentication methods,” such as those used by Bitcoin, “to validate blockchain transactions” (hereinafter, the “Moratorium”).
In other words, the Moratorium singles out for regulation one of many different types of cryptocurrency protocol consensus algorithms. And it singles out for regulation the users — “miners” or “validators” — of one specific type of algorithm.
The Moratorium, if signed into law by the governor, will violate proof-of-work miners’ rights to free speech under the First Amendment.
This is because proof-of-work miners engage in protected speech by broadcasting blocks of data across a protocol’s network. In fact, Bitcoin’s pseudonymous creator, Satoshi Nakamoto, explained that proof-of-work miners are engaged in “publishing” data for the world to see on an immutable, distributed “timestamp server.” The Moratorium singles out block publishers on proof-of-work protocols for a financial burden not borne by block publishers of protocols using other consensus mechanisms. As this article will show, such content-based differentiation is unsustainable under the U.S. Supreme Court’s First Amendment precedent.
The Moratorium thus provides a well-tailored case study to demonstrate that proof-of-work miners, especially Bitcoin miners, are engaged in protected speech under the First Amendment. If such a precedent could, one day, be established, it would provide a strong defense for the proof-of-work mining industry (and Bitcoin itself) against burdensome regulations such as the Moratorium, or even outright bans.
To be clear, the argument presented here is not that Bitcoin itself is speech. While that argument can be made (as Justin Wales expertly demonstrated in his foundational law review article “Bitcoin is Speech: Notes Toward Developing Conceptual Contours Of Its Protection Under The First Amendment,” and as Allen Farrington identified in “Bitcoin is Venice”), that argument is unnecessarily broad for purposes of addressing the Moratorium. And, more fundamentally, we are too early for such a transformative argument. The judiciary is simply not conversant enough with the technological, economical, psychological and philosophical underpinnings of Bitcoin to render a well-reasoned decision on whether Bitcoin is speech. The time will come. But we will get there incrementally, as the judiciary learns and applies its growing knowledge to each case it considers and each precedent it creates about Bitcoin.
So let’s start that process here, with our first case study on Bitcoin as speech, in the narrow context of proof-of-work mining.
This article first establishes that miners in a proof-of-work protocol are engaged in speech as contemplated by the First Amendment. We’ll focus on Bitcoin as our example, because this is Bitcoin Magazine, and because of Bitcoin’s overwhelming share of the proof-of-work market. Next, the article will examine how proof-of-work miner speech is burdened by the Moratorium. Finally, the article will analyze the Moratorium under the different levels of constitutional scrutiny implicated by it.
The Role Of Miners
To understand how Bitcoin miners are engaged in speech, one must understand what miners do, and how they do it.
This requires first dispelling a common misconception about Bitcoin miners. A miner’s primary job in the Bitcoin protocol is not to issue new bitcoin. Andreas Antonopoulos explains it best in “The Internet Of Money Volume Two”:
“Mining doesn’t work to create bitcoin. That is not the purpose of mining; that is a side effect. The way I can prove it’s a side effect is that one day, there will be no new bitcoin. But guess what? There will still be mining. Even after the last satoshi (the smallest unit of bitcoin) gets mined, mining continues. It must continue because its purpose is not to create bitcoin but to provide security, to provide validation of all of the transactions and blocks according to the consensus rules. Generating bitcoin is a side effect that currently serves as a mechanism of reward, creating game-theory incentives to make sure that the validation is done right. Once you understand that and you realize what we’re paying for is security, it changes the perspective slightly.”
“Changes the perspective,” indeed. “Miners” aren’t really miners at all. They are transaction validators. As Darin Feinstein has pointed out, the term “miner” misrepresents the true nature of these nodes in the Bitcoin network: they are accountants auditing the ledger. The term “miner” conjures images of some type of dirty, industrial process of pulling resources out of the ground. That doesn’t sound like speech.
What does sound a lot like speech is Nakamoto’s description of the auditing process in his white paper, the foundational document they used to introduce and explain their creation. Nakamoto did not use the noun “miner,” but they did use the verb “publish.” Explaining how Bitcoin solves the double-spend problem, Nakamoto wrote:
“The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be timestamped and widely publishing the hash, such as in a newspaper or Usenet post [2-5]. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.”
And, to “implement a distributed timestamp server on a peer-to-peer basis,” Nakamoto implemented “a proof-of-work system …, rather than newspaper or Usenet posts,” which democratized and decentralized the process of publishing blocks “to record a public history of transactions” on the time chain, or blockchain.
In other words, the role of Bitcoin miners is to “validate new transactions and record them on the global ledger.” Miners do this by aggregating together pending transactions that comply with the Bitcoin software’s rules and including them in a candidate block that the mining node will publish to the blockchain if it wins the proof-of-work contest for that round.
Proof-Of-Work Primer
Let’s take a moment to examine how that proof-of-work contest functions, so we can better understand the data that miners are processing and writing to the ledger.
First, a simple analogy: Miners compete to find a winning lottery ticket that grants them the ability to publish transactions to the blockchain. As Yan Pritzker wrote in “Inventing Bitcoin”:
“The concept behind Proof of Work is that you participate in a random process, similar to rolling a die. But instead of a six sided die, this one has about as many sides as there are atoms in the universe. In order to roll the die and generate lottery numbers, your computer must perform operations that cost you in terms of electricity.
“To win the lottery, you must produce a number which is mathematically derived from the transactions you want to write to the ledger plus the value of the die you rolled. In order to find this winning number, you may have to roll this die billions, trillions, or quadrillions of times, burning thousands of dollars worth of energy. Since the process is based on randomness, it is possible for everyone to generate their own lottery tickets without a central authority using just a random number generating computer and a list of transactions they want to write to the ledger.”
Next, some details. To generate winning lottery numbers, miners use the SHA-256 hash function, or algorithm, as described by Pritzker:
“The algorithm for proof of work involves repeatedly hashing the header of the block and a random number with the SHA256 cryptographic algorithm until a solution matching a predetermined pattern emerges. The first miner to find such a solution wins the round of competition and publishes that block into the blockchain.”
Hash functions like SHA-256 take in data and produce a large, random number, called a hash. A hash is like a digital fingerprint, because “the output is deterministic: you always get the same output for the same input,” and it is “infeasible to find two strings that hash to the same output,” per Pritzker.
Source: Yan Pritzker, “Inventing Bitcoin” (2019).
The SHA-256 proof-of-work function is also a one-way function, meaning it is impossible to derive the input given only the output. But it is also asymmetric: given the input, anyone can run the algorithm once and verify the output. Thus, while it takes a miner many tries, using substantial compute power and energy, to produce a winning hash, it only takes a fraction of a second to verify the winning hash by the rest of the network.
To produce a hash for entry into the lottery, miners input the block header, plus a nonce, a number used only once. If the output hash is smaller than the target number (set by the Bitcoin software), the miner wins the right to publish the block that round.
Source: Yan Pritzker, “Inventing Bitcoin” (2019).
So there you have it, that’s proof of work.
Proof-Of-Work Miners Publish Facts And Opinions
With this background on proof of work in mind, we can now examine in detail the types of information miners publish. Data published in a winning block includes all pending transactions that fit within the block’s space limitation, metadata and arbitrary data that the miners choose to include.
Specifically, miners write the following data into blocks:
- The list of transactions;
- The block header, which includes
- timestamp,
- the protocol version,
- previous block’s hash (winning lottery number),
- block’s Merkle root (hash of the list summarizing the block’s transactions),
- the difficulty target number,
- and the nonce (the arbitrary number used as part of input for the proof-of-work computation);
- The generation or “coinbase” transaction (not to be confused with the company by the same name) that rewards the miner, comprised of
- transaction fees,
- block subsidy (currently 6.25 bitcoin), and
- miner’s bitcoin address to receive transaction;
- Coinbase data, which can include arbitrary messages from the miner.
Although the mining process runs on computer code, block creation is not entirely predetermined. That is, it reflects deliberate choices that miners have made about which data to include. For example, miners can choose whether to include transactions with no fees (space permitting), and on which basis to include no-fee transactions. Miners also choose what messages to include in the coinbase transaction, from simply stating their name, to signaling support for proposals to upgrade Bitcoin’s software (called soft forks).
Indeed, this signaling process for software upgrades is akin to voting, or, at a minimum, a non-binding straw poll. Before Bitcoin’s most recent major upgrade, known as “Taproot,” mining pools (groups of miners pooling their hashing power together) included a message in their blocks signaling whether they intended to upgrade their software to accommodate the update. Miner votes were not necessary to implement the upgrade, but their indications of support meant that the transition would be a lot smoother.
Another example of a political message in coinbase data is found in the genesis block itself, the first block mined by Nakamoto: “The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.”
This was a newspaper headline from the date of release. It was also a political statement about government interference in money.
Once a miner finds a valid hash under the target number, it broadcasts its candidate block (with all its data, including the proof-of-work solution, visible for anyone to verify) across the Bitcoin network for validation by the other nodes. If the proof-of-work is valid (the miner expended the resources to generate a valid hash under the target), the nodes will include the block in their copies of the blockchain. Through this process, miners publish data contained within the block to the decentralized blockchain in perpetuity.
The Supreme Court has long held “that the creation and dissemination of information are speech within the meaning of the First Amendment.” As explained above, creating and disseminating information are quintessential actions of proof-of-work mining nodes, not mere byproducts. Miners exist to construct candidate blocks containing details of thousands of verified transactions, as well as other data, for publishing and inclusion in the protocol’s blockchain. This process of propagating verifiable facts across the protocol’s network of nodes is, therefore, speech.
“Facts, after all, are the beginning point for much of the speech that is most essential to advance human knowledge and to conduct human affairs,” the Supreme Court has argued.
Additionally, blocks reflect opinions held by miners, which range from the practical to the political.
Proof-of-work miners, therefore, quite clearly engage in speech. “[I]f the acts of ‘disclosing’ and ‘publishing’ information do not constitute speech, it is hard to imagine what does fall within that category.”
The Moratorium Singles Out Proof-Of-Work Publishers For Financial Burdens
The Moratorium is not an outright ban on proof-of-work algorithms. Instead, it places economic burdens on those mining companies running proof-of-work algorithms. But “[l]awmakers may no more silence unwanted speech by burdening its utterance than by censoring its content.”
The Moratorium burdens proof-of-work miners by preventing access to lower-cost sources of electricity (for example, natural gas power plants). As currently drafted, it requires the New York Department of Environmental Conservation (DEC) to deny air pollution permits to any electric-generating facility that utilizes a carbon-based fuel and that provides, in whole or in part, behind-the-meter electric energy consumed or utilized by cryptocurrency mining operations that use proof-of-work authentication methods to validate blockchain transactions.
And renewal applications will not be granted to these same carbon-based electricity providers if they seek contracts that would increase the energy consumed by proof-of-work miners.
Electricity is the necessary input of any data center, and represents the vast majority of any mining company’s operating expense. By limiting new and increased contracts for behind-the-meter electricity at carbon-based power plants, the Moratorium forces proof-of-work miners in New York to find alternative sources of energy, which are often more expensive. The Moratorium thus imposes a significant economic burden on proof-of-work miners — a burden not imposed on other data center operators or cryptocurrency protocol validators — solely due to the content of the data they process and publish (e.g., solutions to proof-of-work algorithms and transactions generated pursuant to the rules of the respective proof-of-work protocol).
The Supreme Court has not hesitated to strike down laws that impose economic burdens on speakers. In “Minneapolis Star & Tribune Co. v. Minnesota Commissioner of Revenue,” the Court invalidated a use tax on “paper and ink products consumed in the production of a publication.” This was a tax borne only by the press, and it only applied to a small subset of the press (publications that consumed more than $100,000 worth of ink and paper). Even though Minnesota did not impose an outright ban on specific content, the Court nonetheless found that this economic burden, which applied differentially to the press, was unconstitutional.
Electricity is to a proof-of-work miner what paper and ink are to a newspaper publisher: a component consumed in the process of publishing. Like the use tax in “Minneapolis Star & Tribune Co.,” the Moratorium imposes a financial burden by increasing the cost of “behind-the-meter electric energy consumed” in the publishing process, which burden is borne only by a specific category of speaker. And the Moratorium is even more “repugnant to First Amendment principles” than the use tax in “Minneapolis Star & Tribune Co.,” because the Moratorium imposes its burden by drawing content-based lines.
For that reason, the Moratorium bears similarities to a sales tax struck down in “Arkansas Writers’ Project, Inc. v. Ragland,” which taxed general interest magazines, but exempted newspapers, religious, professional, trade and sports journals. In comparing the Arkansas sales tax to the use tax in “Minneapolis Star & Tribune Co.,” the Court was particularly troubled by its content-based nature:
“Indeed, this case involves a more disturbing use of selective taxation than Minneapolis Star, because the basis on which Arkansas differentiates between magazines is particularly repugnant to First Amendment principles: a magazine’s tax status depends entirely on its content. Above all else, the First Amendment means that government has no power to restrict expression because of its message, its ideas, its subject matter, or its content. Regulations which permit the Government to discriminate on the basis of the content of the message cannot be tolerated under the First Amendment.”
Like the magazine tax in “Ragland,” whether the Moratorium applies to any particular protocol “depends entirely on its content.” Thus, and as argued more fully in the next section, the Moratorium’s content-based financial burden should be examined under the strictest scrutiny.
That Bitcoin miners are not part of the institutional press nor mainstream media does not deprive them of the protections enjoyed by the newspaper and magazine publishers in the foregoing examples. The Supreme Court in “Citizens United v. Federal Election Commission” found such protections applied to a corporation formed to distribute political media, reiterating that:
“We have consistently rejected the proposition that the institutional press has any constitutional privilege beyond that of other speakers. With the advent of the Internet and the decline of print and broadcast media, moreover, the line between the media and others who wish to comment on political and social issues becomes far more blurred.”
The Court also rejected arguments to diminish protections based on the medium used to publish speech. The Court declared it would not “draw, and then redraw, constitutional lines based on the particular media or technology used to disseminate political speech from a particular speaker,” which would have further chilling effects and amount to a violation of the First Amendment by the judiciary itself.
It makes no difference to the First Amendment that Bitcoin miners use the Bitcoin protocol and proof-of-work algorithm, rather than newspapers, to publish information.
The State of New York might defend the Moratorium by minimizing the burden to proof-of-work miners as a “temporary” pause on new and increased contracts for carbon-based energy, not a permanent ban or burden on compensation.
But the Supreme Court rejected a similar temporal argument in “Simon & Schuster, Inc. v. Members of the New York State Crime Victims Board,” when it struck down a New York law requiring convicted criminals to escrow the proceeds from any sales of media depicting or recounting their crimes, in order to compensate victims. In “Simon & Schuster,” the publisher sued after New York enforced this law against it and Henry Hill, the infamous mobster-author of “Wiseguy,” an autobiography detailing Hill’s life as a “made man” for the New York mob (which Martin Scorsese turned into the Oscar-winning film “Goodfellas”).
New York tried to distinguish its escrow law from the tax in “Ragland” by emphasizing that it did not confiscate funds outright, but held them for a period of time, after which, if no claims were made by victims, the funds would be returned to the author. The Supreme Court rejected this distinction out of hand, stating “this difference can hardly serve as the basis for disparate treatment under the First Amendment,” because both the escrow law and sales tax in “Ragland” were “forms of financial burden” that “operate[d] as disincentives to speak.”
Likewise, here, the Moratorium may be temporary, but it nonetheless “operate[s] as [a] disincentive[] to speak.” Moreover, there is nothing preventing the “temporary” Moratorium from morphing into a permanent ban on the sale of “behind-the-meter electric energy consumed or utilized by cryptocurrency mining operations that use proof-of-work” by carbon-fuel-based electricity generators. (Indeed, a group of U.S. Senators recently has proposed just such a total ban on carbon-fuel-based energy to proof-of-work miners.)
The foregoing authorities demonstrate that the economic burdens imposed by the Moratorium are cognizable under the Supreme Court’s First Amendment jurisprudence.
The Moratorium Fails To Pass Any Level Of Scrutiny Applied
Content-Based Regulations — Strict Scrutiny
The Moratorium imposes a burden on speech that is created as a result of, and in furtherance of, proof-of-work consensus protocols, but no other types of consensus mechanisms. It also specifically singles out two classes of speakers: One, proof-of-work miners and two, carbon-fuel-based electricity providers that supply behind-the-meter electricity to those proof-of-work miners.
Thus, the Moratorium “imposes more than an incidental burden on protected expression. Both on its face and in its practical operation, [New York’s] law imposes a burden based on the content of speech and the identity of the speaker.”
The Court recently reiterated the test for determining whether a regulation is content-based:
“[A] law is content-based if a regulation of speech on its face draws distinctions based on the message a speaker conveys. That description applies to a law that singles out specific subject matter for differential treatment. For example, a law banning the use of sound trucks for political speech — and only political speech — would be a content-based regulation, even if it imposed no limits on the political viewpoints that could be expressed.”
The Moratorium undeniably “singles out specific subject matter” — proof-of-work algorithms — “for differential treatment.” No other cryptocurrency consensus mechanisms or algorithms are subject to the Moratorium’s freeze on carbon-fuel-based energy consumption. When determining whether to issue new or renewed air licenses to carbon-fuel-based energy providers, the Department of Environmental Conservation “must necessarily examine the content of the message that is conveyed” by any behind-the-meter cryptocurrency miners colocated at that energy provider. If the blocks published by miners colocated with the electricity provider contain solutions to proof-of-work algorithms and transaction data for cryptocurrency protocols secured by proof-of-work consensus mechanisms, the Department is prohibited from issuing the license.
“A statute is presumptively inconsistent with the First Amendment if it imposes a financial burden on speakers because of the content of their speech.” Accordingly, a “law that is content-based is subject to strict scrutiny.” Under strict scrutiny, the government bears the burden of proving:
- “its regulation is necessary to serve a compelling state interest,” and
- “is narrowly drawn to achieve that end.”
Under this standard, laws are almost invariably declared unconstitutional. The highest level of scrutiny applies to content-based laws because:
“Above all else, the First Amendment means that government has no power to restrict expression because of its message, its ideas, its subject matter, or its content. Regulations which permit the Government to discriminate on the basis of the content of the message cannot be tolerated under the First Amendment.”
Applying strict scrutiny, we first ascertain New York’s interest served by the Moratorium. The legislative findings included with the enacting bill identify “climate change” as a threat to the state. The bill continues, “[i]t is the policy of the State of New York to conserve, improve and protect its natural resources and environment and to prevent, abate and control water, land and air pollution.” And the bill identifies a concrete goal to reduce “statewide greenhouse gas emissions [by] … eighty-five percent by 2050 and that the state has net zero emissions in all sectors of the economy by that time.”
To be sure, the prevention of climate change and protection of the state’s natural environment are indeed weighty interests. There is little authority, however, on where this nebulous interest lies on the spectrum from “rational basis” (most deferential to government) to “compelling” (least deferential).
But even assuming for purposes of argument that climate change does present a compelling state interest, it is impossible for the state to prove that freezing greenhouse gas emissions at current levels from a single subset of only one industry is “narrowly drawn” to prevent climate change and protect the environment. Even if the State of New York froze all emissions within its borders, private and business-related, at current levels indefinitely, this would have negligible impacts on climate change. Climate change is a global phenomenon.
Nor is the Moratorium on proof-of-work cryptocurrency mining emissions narrowly drawn to achieve the state’s goal of reducing emissions by 85% by 2050 and rendering “all sectors of the economy” net-zero. Again, proof-of-work mining is but one subset of one industry within the New York economy.
There is no meritorious argument the state can marshal to rebut the presumption of unconstitutionality under a strict scrutiny analysis.
Commercial Speech — Intermediate Scrutiny
Proof-of-work data might also be considered commercial speech, as it could be argued that it “propose[s] a commercial transaction.” This is, of course, not accurate, as the transaction data published by miners is almost always between other parties involving transactions to which miners are not a party. Moreover, miners publish blocks that contain data beyond mere transactional facts, as previously established, including political opinions. Nevertheless, a judge operating with a superficial understanding of proof-of-work mining could reach for an easy heuristic like commercial speech.
But “even speech that does no more than propose a commercial transaction is protected by the First Amendment.” Speech proposing a commercial transaction is, however, “entitled to lesser protection than other constitutionally guaranteed expression.”
For commercial speech to be regulated under intermediate or heightened scrutiny:
- the speech must relate to “lawful activity and not be misleading”;
- the governmental interest must be “substantial”; and
- the law must “directly advance[] the governmental interest asserted,” and not be “more extensive than is necessary to serve that interest.”
In other words, “[t]here must be a fit between the legislature’s ends and the means chosen to accomplish those ends.”
Proof-of-work miners, by their nature, publish truthful facts about transactions that are verified by the protocol’s network of nodes. This is a lawful activity and not misleading.
Thus, under intermediate scrutiny, the state will have to prove the Moratorium “directly advances” a “substantial interest.” Again, the law is unsettled on where general climate change and greenhouse emissions goals fall within the spectrum of governmental interests. But even under intermediate scrutiny, the state cannot show that its targeting of a single subset of one single greenhouse-gas-emitting industry “directly advances” its climate goals, for the reasons discussed above.
While this is an easier standard for the state to meet, the Moratorium is simply too underinclusive and ineffective at its stated goals to pass any level of scrutiny applied. Nonetheless, any action challenging the Moratorium should avoid classification of proof-of-work block publishing as pure commercial speech in order to establish a precedent securing the highest levels of protection.
Conclusion
Miners securing cryptocurrency protocols through proof-of-work algorithms, such as Bitcoin, are publishers engaged in speech entitled to First Amendment protections of the highest order. Because of this, any law or regulation affecting proof-of-work miners must be generally applicable and content neutral. Laws such as the Moratorium in New York Assembly Bill A7389C, which target proof-of-work miners based on the content of their speech, violate miners’ First Amendment rights and should be invalidated.
Thus, the Moratorium (once signed into law) provides a meaningful opportunity for a test case to establish favorable precedent shielding the proof-of-work mining industry from burdensome regulation — and even outright bans. And, because the issue of whether the Moratorium is narrowly drawn to prevent climate change would be litigated in such a case, it would also provide an opportunity to dispel energy misinformation and fear, uncertainty and doubt (FUD), based on credible expert testimony and judicial fact-finding. Such a case could shift the narrative on Bitcoin mining and demonstrate the incredible benefits proof-of-work protocols provide to society.
The goal of this article has been to spark thoughtful argument and debate on an important issue pertinent to Bitcoin and Constitutional rights. Please feel free to contribute to the discussion on Twitter, or by email.
This is a guest post by Aaron Daniel. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.

Crypto
El Salvador Takes First Step To Issue Bitcoin Volcano Bonds
Published
2 years agoon
November 22, 2022
El Salvador’s Minister of the Economy Maria Luisa Hayem Brevé submitted a digital assets issuance bill to the country’s legislative assembly, paving the way for the launch of its bitcoin-backed “volcano” bonds.
First announced one year ago today, the pioneering initiative seeks to attract capital and investors to El Salvador. It was revealed at the time the plans to issue $1 billion in bonds on the Liquid Network, a federated Bitcoin sidechain, with the proceedings of the bonds being split between a $500 million direct allocation to bitcoin and an investment of the same amount in building out energy and bitcoin mining infrastructure in the region.
A sidechain is an independent blockchain that runs parallel to another blockchain, allowing for tokens from that blockchain to be used securely in the sidechain while abiding by a different set of rules, performance requirements, and security mechanisms. Liquid is a sidechain of Bitcoin that allows bitcoin to flow between the Liquid and Bitcoin networks with a two-way peg. A representation of bitcoin used in the Liquid network is referred to as L-BTC. Its verifiably equivalent amount of BTC is managed and secured by the network’s members, called functionaries.
“Digital securities law will enable El Salvador to be the financial center of central and south America,” wrote Paolo Ardoino, CTO of cryptocurrency exchange Bitfinex, on Twitter.
Bitfinex is set to be granted a license in order to be able to process and list the bond issuance in El Salvador.
The bonds will pay a 6.5% yield and enable fast-tracked citizenship for investors. The government will share half the additional gains with investors as a Bitcoin Dividend once the original $500 million has been monetized. These dividends will be dispersed annually using Blockstream’s asset management platform.
The act of submitting the bill, which was hinted at earlier this year, kickstarts the first major milestone before the bonds can see the light of day. The next is getting it approved, which is expected to happen before Christmas, a source close to President Nayib Bukele told Bitcoin Magazine. The bill was submitted on November 17 and presented to the country’s Congress today. It is embedded in full below.
Crypto
How I’ll Talk To Family Members About Bitcoin This Thanksgiving
Published
2 years agoon
November 22, 2022
This is an opinion editorial by Joakim Book, a Research Fellow at the American Institute for Economic Research, contributor and copy editor for Bitcoin Magazine and a writer on all things money and financial history.
I don’t.
That’s it. That’s the article.
In all sincerity, that is the full message: Just don’t do it. It’s not worth it.
You’re not an excited teenager anymore, in desperate need of bragging credits or trying out your newfound wisdom. You’re not a preaching priestess with lost souls to save right before some imminent arrival of the day of reckoning. We have time.
Instead: just leave people alone. Seriously. They came to Thanksgiving dinner to relax and rejoice with family, laugh, tell stories and zone out for a day — not to be ambushed with what to them will sound like a deranged rant in some obscure topic they couldn’t care less about. Even if it’s the monetary system, which nobody understands anyway.
Get real.
If you’re not convinced of this Dale Carnegie-esque social approach, and you still naively think that your meager words in between bites can change anybody’s view on anything, here are some more serious reasons for why you don’t talk to friends and family about Bitcoin the protocol — but most certainly not bitcoin, the asset:
- Your family and friends don’t want to hear it. Move on.
- For op-sec reasons, you don’t want to draw unnecessary attention to the fact that you probably have a decent bitcoin stack. Hopefully, family and close friends should be safe enough to confide in, but people talk and that gossip can only hurt you.
- People find bitcoin interesting only when they’re ready to; everyone gets the price they deserve. Like Gigi says in “21 Lessons:”
“Bitcoin will be understood by you as soon as you are ready, and I also believe that the first fractions of a bitcoin will find you as soon as you are ready to receive them. In essence, everyone will get ₿itcoin at exactly the right time.”
It’s highly unlikely that your uncle or mother-in-law just happens to be at that stage, just when you’re about to sit down for dinner.
- Unless you can claim youth, old age or extreme poverty, there are very few people who genuinely haven’t heard of bitcoin. That means your evangelizing wouldn’t be preaching to lost, ignorant souls ready to be saved but the tired, huddled and jaded masses who could care less about the discovery that will change their societies more than the internal combustion engine, internet and Big Government combined. Big deal.
- What is the case, however, is that everyone in your prospective audience has already had a couple of touchpoints and rejected bitcoin for this or that standard FUD. It’s a scam; seems weird; it’s dead; let’s trust the central bankers, who have our best interest at heart.
No amount of FUD busting changes that impression, because nobody holds uninformed and fringe convictions for rational reasons, reasons that can be flipped by your enthusiastic arguments in-between wiping off cranberry sauce and grabbing another turkey slice. - It really is bad form to talk about money — and bitcoin is the best money there is. Be classy.
Now, I’m not saying to never ever talk about Bitcoin. We love to talk Bitcoin — that’s why we go to meetups, join Twitter Spaces, write, code, run nodes, listen to podcasts, attend conferences. People there get something about this monetary rebellion and have opted in to be part of it. Your unsuspecting family members have not; ambushing them with the wonders of multisig, the magically fast Lightning transactions or how they too really need to get on this hype train, like, yesterday, is unlikely to go down well.
However, if in the post-dinner lull on the porch someone comes to you one-on-one, whisky in hand and of an inquisitive mind, that’s a very different story. That’s personal rather than public, and it’s without the time constraints that so usually trouble us. It involves clarifying questions or doubts for somebody who is both expressively curious about the topic and available for the talk. That’s rare — cherish it, and nurture it.
Last year I wrote something about the proper role of political conversations in social settings. Since November was also election month, it’s appropriate to cite here:
“Politics, I’m starting to believe, best belongs in the closet — rebranded and brought out for the specific occasion. Or perhaps the bedroom, with those you most trust, love, and respect. Not in public, not with strangers, not with friends, and most certainly not with other people in your community. Purge it from your being as much as you possibly could, and refuse to let political issues invade the areas of our lives that we cherish; politics and political disagreements don’t belong there, and our lives are too important to let them be ruled by (mostly contrived) political disagreements.”
If anything, those words seem more true today than they even did then. And I posit to you that the same applies for bitcoin.
Everyone has some sort of impression or opinion of bitcoin — and most of them are plain wrong. But there’s nothing people love more than a savior in white armor, riding in to dispel their errors about some thing they are freshly out of fucks for. Just like politics, nobody really cares.
Leave them alone. They will find bitcoin in their own time, just like all of us did.
This is a guest post by Joakim Book. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.

This is an opinion editorial by Federico Tenga, a long time contributor to Bitcoin projects with experience as start-up founder, consultant and educator.
The term “smart contracts” predates the invention of the blockchain and Bitcoin itself. Its first mention is in a 1994 article by Nick Szabo, who defined smart contracts as a “computerized transaction protocol that executes the terms of a contract.” While by this definition Bitcoin, thanks to its scripting language, supported smart contracts from the very first block, the term was popularized only later by Ethereum promoters, who twisted the original definition as “code that is redundantly executed by all nodes in a global consensus network”
While delegating code execution to a global consensus network has advantages (e.g. it is easy to deploy unowed contracts, such as the popularly automated market makers), this design has one major flaw: lack of scalability (and privacy). If every node in a network must redundantly run the same code, the amount of code that can actually be executed without excessively increasing the cost of running a node (and thus preserving decentralization) remains scarce, meaning that only a small number of contracts can be executed.
But what if we could design a system where the terms of the contract are executed and validated only by the parties involved, rather than by all members of the network? Let us imagine the example of a company that wants to issue shares. Instead of publishing the issuance contract publicly on a global ledger and using that ledger to track all future transfers of ownership, it could simply issue the shares privately and pass to the buyers the right to further transfer them. Then, the right to transfer ownership can be passed on to each new owner as if it were an amendment to the original issuance contract. In this way, each owner can independently verify that the shares he or she received are genuine by reading the original contract and validating that all the history of amendments that moved the shares conform to the rules set forth in the original contract.
This is actually nothing new, it is indeed the same mechanism that was used to transfer property before public registers became popular. In the U.K., for example, it was not compulsory to register a property when its ownership was transferred until the ‘90s. This means that still today over 15% of land in England and Wales is unregistered. If you are buying an unregistered property, instead of checking on a registry if the seller is the true owner, you would have to verify an unbroken chain of ownership going back at least 15 years (a period considered long enough to assume that the seller has sufficient title to the property). In doing so, you must ensure that any transfer of ownership has been carried out correctly and that any mortgages used for previous transactions have been paid off in full. This model has the advantage of improved privacy over ownership, and you do not have to rely on the maintainer of the public land register. On the other hand, it makes the verification of the seller’s ownership much more complicated for the buyer.

Source: Title deed of unregistered real estate propriety
How can the transfer of unregistered properties be improved? First of all, by making it a digitized process. If there is code that can be run by a computer to verify that all the history of ownership transfers is in compliance with the original contract rules, buying and selling becomes much faster and cheaper.
Secondly, to avoid the risk of the seller double-spending their asset, a system of proof of publication must be implemented. For example, we could implement a rule that every transfer of ownership must be committed on a predefined spot of a well-known newspaper (e.g. put the hash of the transfer of ownership in the upper-right corner of the first page of the New York Times). Since you cannot place the hash of a transfer in the same place twice, this prevents double-spending attempts. However, using a famous newspaper for this purpose has some disadvantages:
- You have to buy a lot of newspapers for the verification process. Not very practical.
- Each contract needs its own space in the newspaper. Not very scalable.
- The newspaper editor can easily censor or, even worse, simulate double-spending by putting a random hash in your slot, making any potential buyer of your asset think it has been sold before, and discouraging them from buying it. Not very trustless.
For these reasons, a better place to post proof of ownership transfers needs to be found. And what better option than the Bitcoin blockchain, an already established trusted public ledger with strong incentives to keep it censorship-resistant and decentralized?
If we use Bitcoin, we should not specify a fixed place in the block where the commitment to transfer ownership must occur (e.g. in the first transaction) because, just like with the editor of the New York Times, the miner could mess with it. A better approach is to place the commitment in a predefined Bitcoin transaction, more specifically in a transaction that originates from an unspent transaction output (UTXO) to which the ownership of the asset to be issued is linked. The link between an asset and a bitcoin UTXO can occur either in the contract that issues the asset or in a subsequent transfer of ownership, each time making the target UTXO the controller of the transferred asset. In this way, we have clearly defined where the obligation to transfer ownership should be (i.e in the Bitcoin transaction originating from a particular UTXO). Anyone running a Bitcoin node can independently verify the commitments and neither the miners nor any other entity are able to censor or interfere with the asset transfer in any way.
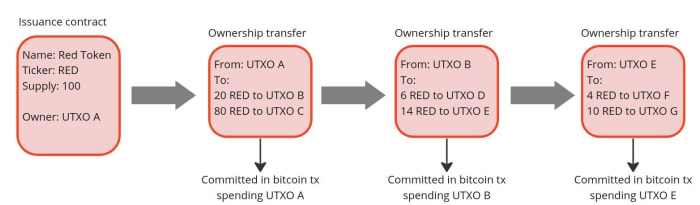
Since on the Bitcoin blockchain we only publish a commitment of an ownership transfer, not the content of the transfer itself, the seller needs a dedicated communication channel to provide the buyer with all the proofs that the ownership transfer is valid. This could be done in a number of ways, potentially even by printing out the proofs and shipping them with a carrier pigeon, which, while a bit impractical, would still do the job. But the best option to avoid the censorship and privacy violations is establish a direct peer-to-peer encrypted communication, which compared to the pigeons also has the advantage of being easy to integrate with a software to verify the proofs received from the counterparty.
This model just described for client-side validated contracts and ownership transfers is exactly what has been implemented with the RGB protocol. With RGB, it is possible to create a contract that defines rights, assigns them to one or more existing bitcoin UTXO and specifies how their ownership can be transferred. The contract can be created starting from a template, called a “schema,” in which the creator of the contract only adjusts the parameters and ownership rights, as is done with traditional legal contracts. Currently, there are two types of schemas in RGB: one for issuing fungible tokens (RGB20) and a second for issuing collectibles (RGB21), but in the future, more schemas can be developed by anyone in a permissionless fashion without requiring changes at the protocol level.
To use a more practical example, an issuer of fungible assets (e.g. company shares, stablecoins, etc.) can use the RGB20 schema template and create a contract defining how many tokens it will issue, the name of the asset and some additional metadata associated with it. It can then define which bitcoin UTXO has the right to transfer ownership of the created tokens and assign other rights to other UTXOs, such as the right to make a secondary issuance or to renominate the asset. Each client receiving tokens created by this contract will be able to verify the content of the Genesis contract and validate that any transfer of ownership in the history of the token received has complied with the rules set out therein.
So what can we do with RGB in practice today? First and foremost, it enables the issuance and the transfer of tokenized assets with better scalability and privacy compared to any existing alternative. On the privacy side, RGB benefits from the fact that all transfer-related data is kept client-side, so a blockchain observer cannot extract any information about the user’s financial activities (it is not even possible to distinguish a bitcoin transaction containing an RGB commitment from a regular one), moreover, the receiver shares with the sender only blinded UTXO (i. e. the hash of the concatenation between the UTXO in which she wish to receive the assets and a random number) instead of the UTXO itself, so it is not possible for the payer to monitor future activities of the receiver. To further increase the privacy of users, RGB also adopts the bulletproof cryptographic mechanism to hide the amounts in the history of asset transfers, so that even future owners of assets have an obfuscated view of the financial behavior of previous holders.
In terms of scalability, RGB offers some advantages as well. First of all, most of the data is kept off-chain, as the blockchain is only used as a commitment layer, reducing the fees that need to be paid and meaning that each client only validates the transfers it is interested in instead of all the activity of a global network. Since an RGB transfer still requires a Bitcoin transaction, the fee saving may seem minimal, but when you start introducing transaction batching they can quickly become massive. Indeed, it is possible to transfer all the tokens (or, more generally, “rights”) associated with a UTXO towards an arbitrary amount of recipients with a single commitment in a single bitcoin transaction. Let’s assume you are a service provider making payouts to several users at once. With RGB, you can commit in a single Bitcoin transaction thousands of transfers to thousands of users requesting different types of assets, making the marginal cost of each single payout absolutely negligible.
Another fee-saving mechanism for issuers of low value assets is that in RGB the issuance of an asset does not require paying fees. This happens because the creation of an issuance contract does not need to be committed on the blockchain. A contract simply defines to which already existing UTXO the newly issued assets will be allocated to. So if you are an artist interested in creating collectible tokens, you can issue as many as you want for free and then only pay the bitcoin transaction fee when a buyer shows up and requests the token to be assigned to their UTXO.
Furthermore, because RGB is built on top of bitcoin transactions, it is also compatible with the Lightning Network. While it is not yet implemented at the time of writing, it will be possible to create asset-specific Lightning channels and route payments through them, similar to how it works with normal Lightning transactions.
Conclusion
RGB is a groundbreaking innovation that opens up to new use cases using a completely new paradigm, but which tools are available to use it? If you want to experiment with the core of the technology itself, you should directly try out the RGB node. If you want to build applications on top of RGB without having to deep dive into the complexity of the protocol, you can use the rgb-lib library, which provides a simple interface for developers. If you just want to try to issue and transfer assets, you can play with Iris Wallet for Android, whose code is also open source on GitHub. If you just want to learn more about RGB you can check out this list of resources.
This is a guest post by Federico Tenga. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.