Crypto
The War On Dissent
Published
2 years agoon

This article originally appeared in Bitcoin Magazine’s “Censorship Resistant Issue.” To get a copy, visit our store.
Online censorship is becoming increasingly normalized as growing restrictions, deplatforming and its other manifestations have become so pervasive that many have simply come to accept it. This “new normal” for free speech is as insidious as it has been gradual, as we are increasingly being trained to accept unconstitutional limitations on what we can express on the websites that dominate online socialization. Like so much of our lives, social interaction has moved online at a rapid pace in the last decade, meaning that restrictions imposed upon online speech have a disproportionate effect on speech in general.
The argument that is often deployed to dismiss concerns regarding online censorship is the claim that the dominant social media companies are private, not public, entities. However, in reality, the Big Tech firms that dominate our online lives, particularly Google and Facebook, were either created with some involvement of the U.S. national security state or have become major U.S. government and/or military contractors over the past two decades.(i,ii,iii,iv,v) When it comes to censoring and deplatforming individuals for claims that run counter to U.S. government narratives, it should be clear that Google-owned YouTube, and other tech platforms owned by contractors to the U.S. military and intelligence communities, have a major conflict of interest in their stifling of speech.
The line between “private” Silicon Valley and the public sector has become increasingly blurred and it is now a matter of record that these companies have illegally passed information onto intelligence services, like the National Security Agency (NSA), for blatantly unconstitutional surveillance programs aimed at American civilians.(vi) All indications point to the military-industrial complex having expanded into the military-technology-industrial complex.
These days, one need only look at important government commissions — such as the National Security Commission on Artificial Intelligence (NSCAI), headed by former Google/Alphabet CEO Eric Schmidt — to see how this de facto public-private partnership between Silicon Valley and the national security state functions, and its outsized role in setting important tech-related policies for both the private and public sectors. For example, that commission, largely comprised of representatives of the military, intelligence community and the scions of Big Tech, has helped set policy on “countering disinformation” online. More specifically, it has recommended weaponizing Artificial Intelligence (AI) for the express purpose of identifying online accounts to deplatform and speech to censor, framing this recommendation as essential to U.S. national security as it relates to “information warfare.”(vii,viii)
There are already several companies competing to market an AI-powered censorship engine to the national security state as well as the private sector. One of these companies is Primer AI, a “machine intelligence” company that “builds software machines that read and write in English, Russian, and Chinese to automatically unearth trends and patterns across large volumes of data.” The company publicly states that their work “supports the mission of the intelligence community and broader DOD by automating reading and research tasks to enhance the speed and quality of decision-making.” Their current roster of clients includes the U.S. military, U.S. intelligence, major American companies like Walmart and private “philanthropic” organizations like the Bill & Melinda Gates Foundation.(ix)
Primer’s founder, Sean Gourley, who previously created AI programs for the military to track insurgents in post-invasion Iraq, asserted in an April 2020 blog post that “computational warfare and disinformation campaigns will, in 2020, become a more serious threat than physical war, and we will have to rethink the weapons we deploy to fight them.”(x) In that same post, Gourley argued for the creation of a “Manhattan Project for truth” that would create a publicly available Wikipedia-style database built off of “knowledge bases [that] already exist inside many countries’ intelligence agencies for national security purposes.” Gourley wrote that “this effort would be ultimately about building and enhancing our collective intelligence and establishing a baseline for what’s true or not.” He concludes his blog post by stating that “in 2020, we will begin to weaponize truth.”
Since that year, Primer has been under contract with the U.S. military to “develop the first-ever machine learning platform to automatically identify and assess suspected disinformation.”(xi) That the term “suspected disinformation” was used is no accident, as many instances of online censorship involve merely assertions, as opposed to confirmations, that censored speech is part of a nation state-connected or “bad actor”-connected organized disinformation campaign. While those campaigns do exist, legitimate and constitutionally protected speech that deviates from the “official” or government-sanctioned narrative are frequently censored under these metrics, often with little to no ability to meaningfully appeal the censor’s decision. In other cases, posts “suspected” of being disinformation or that are flagged as such (sometimes erroneously) by social media algorithms, are removed or hidden from public view without the poster’s knowledge.
In addition, “suspected disinformation” can be used to justify the censorship of speech that is inconvenient for particular governments, corporations and groups, as there is no need to have evidence or present a coherent case that said content is disinformation — one must only cast suspicion upon it in order to have it censored. Further complicating this issue is the fact that some claims initially labeled “disinformation” later become accepted fact or recognized as legitimate speech. This has happened on more than one occasion during the COVID-19 crisis, where content creators had their accounts deleted or their content censored just for broaching issues like the lab-leak hypothesis as well as questions over mask and vaccine efficacy, among many other issues.(xii, xiii) A year or two later, much of this supposed “disinformation” was subsequently admitted to include legitimate avenues of journalistic inquiry and the initial, blanket censorship on these topics was done at the behest of public and private actors alike due to their inconvenience to what had once been the prevailing narrative.(xiv, xv)
Primer is only one of several companies seeking to create a world where “truth” is defined by the U.S. national security state, with that rigid definition then being enforced by Big Tech companies with no room for debate. Brian Raymond, a former official for the CIA and the National Security Council who now serves as Primer’s vice president, openly wrote about this in November 2020 for Foreign Policy.
In that article, he stated:
“Companies like Facebook, Twitter, and Google are increasingly working with U.S. defense agencies to educate future software engineers, cybersecurity experts, and scientists. Eventually, once public-private trust is fully restored, the U.S. government and Silicon Valley can forge a united front in order to effectively take on fake news.” (xvi)
Particularly troubling is the fact that Raymond’s chief example of “fake news” at the time was the New York Post’s reporting on the Hunter Biden laptop emails, which — well over a year after the fact — has now been confirmed as authentic.(xvii) Having the government, and more specifically the national security state, which has conducted a litany of confirmed disinformation and propaganda campaigns over the years, define truth and reality is hardly consistent with its professed goal of protecting “democracy.”(xviii) Instead, it protects the interests of the national security state itself, whose own interests are tightly interwoven with those of the country’s increasingly entrenched (and enriched) oligarchy.
Not only do we have the national security state in a de facto public-private partnership with Big Tech to censor online information — Now, with the recent launch of the Biden administration’s war on domestic terror, we have the same national security state framing “suspected disinformation” and “conspiracy theories” as national security threats. The policy documents that outline this new war note that a major “pillar” of the government’s entire strategy is to eliminate online material that they claim promotes “domestic terrorist” ideologies, including those that “connect and intersect with conspiracy theories and other forms of disinformation and misinformation.” The proliferation of “dangerous” information “on Internet-based communications platforms such as social media, file-upload sites and end-to-end encrypted platforms”, it argues, “[…] can combine and amplify threats to public safety.” The “front lines” of this war are “overwhelmingly private-sector online platforms.”
The problem with this framing is that the Biden administration’s definition of “domestic terrorist” used in these same documents is incredibly broad. For example, it labels opposition to corporate globalization, capitalism and government overreach as “terrorist” ideologies. This means that online content discussing “anti-government” and/or “anti-authority” ideas, which may simply be criticisms of government policy or the national power structure, could soon be treated in the same way as online Al Qaeda or ISIS propaganda. In addition, intelligence agencies in both the U.K. and U.S. have moved to treat critical reporting of COVID-19 vaccines and mandates as “extremist” propaganda, despite the fact that a significant percentage of Americans have chosen not to get the vaccine and/or oppose vaccine mandates.
In what appears to be the apparent fulfilment of Primer AI executives’ pleas, the Biden administration also underscores the need to “increase digital literacy” among the American public, while censoring “harmful content” disseminated by “domestic terrorists” as well as by “hostile foreign powers seeking to undermine American democracy.” The latter is a clear reference to the claim that critical reporting of U.S. government policy, particularly its military and intelligence activities abroad, was the product of “Russian disinformation,” a now-discredited claim that was used to heavily censor independent media. Regarding “increasing digital literacy,” the policy documents make it clear that this refers to a new “digital literacy” education curriculum that is currently being developed by the Department of Homeland Security (DHS), the U.S.’ domestically-focused intelligence agency, for a domestic audience. This “digital literacy” initiative would have previously violated U.S. law, until the Obama administration worked with Congress to repeal the Smith-Mundt Act, which lifted the World War II-era ban on the U.S. government directing propaganda at domestic audiences.
The Biden administration’s war on domestic terror policy also makes it clear that the censorship, as described above, is part of a “broader priority” of the administration, which it defines as follows:
“[…] enhancing faith in government and addressing the extreme polarization, fueled by a crisis of disinformation and misinformation often channeled through social media platforms, which can tear Americans apart and lead some to violence.”
In other words, fostering trust in government while simultaneously censoring “polarizing” voices who distrust or criticize the government is a key policy goal behind the Biden administration’s new domestic-terror strategy. In addition, this statement implies that Americans not agreeing with each other is problematic and frames that disagreement as a driver of violence, as opposed to a normal occurrence in a supposed democracy that has constitutional protections for freedom of speech. From this framing, it is implied that such violence can only be stopped if all Americans trust the government and agree with its narratives and “truths.” Framing deviations from these narratives as national security threats, as is done in this policy document, invites the labeling of non-conforming speech as “violence” or as “inciting violence” through the fomentation of disagreement. As a result, those who post non-conforming speech online may soon find themselves being labeled as “terrorists” by the state.
If we are to accept the “new normal” of online censorship, these efforts to prohibit debate and legitimate criticisms of government policy in the name of “national security” will continue unimpeded. In short order, the First Amendment will be redefined so that it only protects government-sanctioned speech, not the freedom of speech, as was intended. While such measures are often framed as necessary to “protect” democracy, the elimination and imminent criminalization of legitimate speech is the true threat to democracy, one that should deeply disturb all Americans. If the national security state controls and enforces the only permissible narratives and the only permitted version of the “truth,” they will then also control human perception, and — as a consequence — human behavior.
Such control has long been a goal of some within the U.S.’ military and intelligence communities, but it is anathema to the values and desires of the vast majority of Americans. If there is no meaningful pushback against the increasing fusion of the national security state and Big Tech, Americans are guaranteed to lose much more than just the freedom of speech, as controlling speech is just the first step towards controlling all behavior. Americans would do well to remember the warning of Benjamin Franklin as the U.S. government moves to criminalize free speech under the guise of protecting national security; “Those who would give up essential liberty, to purchase a little temporary safety, deserve neither liberty nor safety.”
Endnotes:
i Webb, Whitney. “The Military Origins of Facebook.” Unlimited Hangout, 12 Apr. 2021, unlimitedhangout.com/2021/04/investigative-reports/the-military-origins-of-facebook/.
ii Ahmed, Nafeez. “How the CIA Made Google.” Medium, INSURGE intelligence, 22 Jan. 2015, medium.com/insurge-intelligence/how-the-cia-made-google-e836451a959e.
iii Feiner, Lauren. “Google’s Cloud Division Lands Deal with the Department of Defense.” CNBC, 20 May 2020, www.cnbc.com/2020/05/20/googles-cloud-division-lands-deal-with-the-department-of-defense.html.
iv Novet, Jordan. “Microsoft Wins U.S. Army Contract for Augmented Reality Headsets, Worth up to $21.9 Billion over 10 Years.” CNBC, 31 Mar. 2021, www.cnbc.com/2021/03/31/microsoft-wins-contract-to-make-modified-hololens-for-us-army.html.
v Shane, Scott, and Daisuke Wakabayashi. ““The Business of War”: Google Employees Protest Work for the Pentagon.” The New York Times, 4 Apr. 2018, www.nytimes.com/2018/04/04/technology/google-letter-ceo-pentagon-project.html.
vi “Commissioners.” NSCAI, www.nscai.gov/commissioners/.
vii Interim Report and Third Quarter Recommendations. 2020.
viii PrimerAI Homepage.” PrimerAI, primer.ai/.
ix “To Fight Disinformation, We Need to Weaponise the Truth.” PrimerAI, 20 Apr. 2020, primer.ai/blog/to-fight-disinformation-we-need-to-weaponise-the-truth/.
x AI, Primer. “SOCOM and US Air Force Enlist Primer to Combat Disinformation.” www.prnewswire.com, 1 Oct. 2020, www.prnewswire.com/news-releases/socom-and-us-air-force-enlist-primer-to-combat-disinformation-301143716.html/.
xi Forget Counterterrorism, the United States Needs a Counter-Disinformation Strategy.” PrimerAI, 16 Nov. 2020, primer.ai/blog/forget-counterterrorism-the-united-states-needs-a-counter-disinformation/.
xii Golding, Bruce. “Washington Post Joins New York Times in Finally Admitting Emails from Hunter Biden Laptop Are Real.” New York Post, 30 Mar. 2022, nypost.com/2022/03/30/washington-post-admits-hunter-biden-laptop-is-real/.
xiii Greenwald, Glenn. “The CIA’s Murderous Practices, Disinformation Campaigns, and Interference in Other Countries Still Shape the World Order and U.S. Politics.” The Intercept, 21 May 2020, theintercept.com/2020/05/21/the-cias-murderous-practices-disinformation-campaigns-and-interference-in-other-countries-still-shapes-the-world-order-and-u-s-politics/.
xiv Ferreira, Roberto Garcia. “The Cia and Jacobo Arbenz: History of a Disinformation Campaign .” Journal of Third World Studies, vol. 25, no. 2, 2008, pp. 59–81, www.jstor.org/stable/45194479, 10.2307/45194479.f.
xv National Strategy for Countering Domestic Terrorism, June 2021. https://www.whitehouse.gov/wp-content/uploads/2021/06/National-Strategy-for-Countering-Domestic-Terrorism.pdf.
xvi Webb, Whitney. “US – UK Intel Agencies Declare Cyber War on Independent Media.” Unlimitedhangout.com, 11 Nov. 2020, unlimitedhangout.com/2020/11/reports/us-uk-intel-agencies-declare-cyber-war-on-independent-media/.
xvii Webb, Whitney. “Lifting of US Propaganda Ban Gives New Meaning to Old Song.” MintPress News, 12 Feb. 2018, www.mintpressnews.com/planting-stories-in-the-press-lifting-of-us-propaganda-ban-gives-new-meaning-to-old-song/237493/.
xviii National Strategy for Countering Domestic Terrorism, June 2021. https://www.whitehouse.gov/wp-content/uploads/2021/06/National-Strategy-for-Countering-Domestic-Terrorism.pdf/.

Crypto
El Salvador Takes First Step To Issue Bitcoin Volcano Bonds
Published
2 years agoon
November 22, 2022
El Salvador’s Minister of the Economy Maria Luisa Hayem Brevé submitted a digital assets issuance bill to the country’s legislative assembly, paving the way for the launch of its bitcoin-backed “volcano” bonds.
First announced one year ago today, the pioneering initiative seeks to attract capital and investors to El Salvador. It was revealed at the time the plans to issue $1 billion in bonds on the Liquid Network, a federated Bitcoin sidechain, with the proceedings of the bonds being split between a $500 million direct allocation to bitcoin and an investment of the same amount in building out energy and bitcoin mining infrastructure in the region.
A sidechain is an independent blockchain that runs parallel to another blockchain, allowing for tokens from that blockchain to be used securely in the sidechain while abiding by a different set of rules, performance requirements, and security mechanisms. Liquid is a sidechain of Bitcoin that allows bitcoin to flow between the Liquid and Bitcoin networks with a two-way peg. A representation of bitcoin used in the Liquid network is referred to as L-BTC. Its verifiably equivalent amount of BTC is managed and secured by the network’s members, called functionaries.
“Digital securities law will enable El Salvador to be the financial center of central and south America,” wrote Paolo Ardoino, CTO of cryptocurrency exchange Bitfinex, on Twitter.
Bitfinex is set to be granted a license in order to be able to process and list the bond issuance in El Salvador.
The bonds will pay a 6.5% yield and enable fast-tracked citizenship for investors. The government will share half the additional gains with investors as a Bitcoin Dividend once the original $500 million has been monetized. These dividends will be dispersed annually using Blockstream’s asset management platform.
The act of submitting the bill, which was hinted at earlier this year, kickstarts the first major milestone before the bonds can see the light of day. The next is getting it approved, which is expected to happen before Christmas, a source close to President Nayib Bukele told Bitcoin Magazine. The bill was submitted on November 17 and presented to the country’s Congress today. It is embedded in full below.
Crypto
How I’ll Talk To Family Members About Bitcoin This Thanksgiving
Published
2 years agoon
November 22, 2022
This is an opinion editorial by Joakim Book, a Research Fellow at the American Institute for Economic Research, contributor and copy editor for Bitcoin Magazine and a writer on all things money and financial history.
I don’t.
That’s it. That’s the article.
In all sincerity, that is the full message: Just don’t do it. It’s not worth it.
You’re not an excited teenager anymore, in desperate need of bragging credits or trying out your newfound wisdom. You’re not a preaching priestess with lost souls to save right before some imminent arrival of the day of reckoning. We have time.
Instead: just leave people alone. Seriously. They came to Thanksgiving dinner to relax and rejoice with family, laugh, tell stories and zone out for a day — not to be ambushed with what to them will sound like a deranged rant in some obscure topic they couldn’t care less about. Even if it’s the monetary system, which nobody understands anyway.
Get real.
If you’re not convinced of this Dale Carnegie-esque social approach, and you still naively think that your meager words in between bites can change anybody’s view on anything, here are some more serious reasons for why you don’t talk to friends and family about Bitcoin the protocol — but most certainly not bitcoin, the asset:
- Your family and friends don’t want to hear it. Move on.
- For op-sec reasons, you don’t want to draw unnecessary attention to the fact that you probably have a decent bitcoin stack. Hopefully, family and close friends should be safe enough to confide in, but people talk and that gossip can only hurt you.
- People find bitcoin interesting only when they’re ready to; everyone gets the price they deserve. Like Gigi says in “21 Lessons:”
“Bitcoin will be understood by you as soon as you are ready, and I also believe that the first fractions of a bitcoin will find you as soon as you are ready to receive them. In essence, everyone will get ₿itcoin at exactly the right time.”
It’s highly unlikely that your uncle or mother-in-law just happens to be at that stage, just when you’re about to sit down for dinner.
- Unless you can claim youth, old age or extreme poverty, there are very few people who genuinely haven’t heard of bitcoin. That means your evangelizing wouldn’t be preaching to lost, ignorant souls ready to be saved but the tired, huddled and jaded masses who could care less about the discovery that will change their societies more than the internal combustion engine, internet and Big Government combined. Big deal.
- What is the case, however, is that everyone in your prospective audience has already had a couple of touchpoints and rejected bitcoin for this or that standard FUD. It’s a scam; seems weird; it’s dead; let’s trust the central bankers, who have our best interest at heart.
No amount of FUD busting changes that impression, because nobody holds uninformed and fringe convictions for rational reasons, reasons that can be flipped by your enthusiastic arguments in-between wiping off cranberry sauce and grabbing another turkey slice. - It really is bad form to talk about money — and bitcoin is the best money there is. Be classy.
Now, I’m not saying to never ever talk about Bitcoin. We love to talk Bitcoin — that’s why we go to meetups, join Twitter Spaces, write, code, run nodes, listen to podcasts, attend conferences. People there get something about this monetary rebellion and have opted in to be part of it. Your unsuspecting family members have not; ambushing them with the wonders of multisig, the magically fast Lightning transactions or how they too really need to get on this hype train, like, yesterday, is unlikely to go down well.
However, if in the post-dinner lull on the porch someone comes to you one-on-one, whisky in hand and of an inquisitive mind, that’s a very different story. That’s personal rather than public, and it’s without the time constraints that so usually trouble us. It involves clarifying questions or doubts for somebody who is both expressively curious about the topic and available for the talk. That’s rare — cherish it, and nurture it.
Last year I wrote something about the proper role of political conversations in social settings. Since November was also election month, it’s appropriate to cite here:
“Politics, I’m starting to believe, best belongs in the closet — rebranded and brought out for the specific occasion. Or perhaps the bedroom, with those you most trust, love, and respect. Not in public, not with strangers, not with friends, and most certainly not with other people in your community. Purge it from your being as much as you possibly could, and refuse to let political issues invade the areas of our lives that we cherish; politics and political disagreements don’t belong there, and our lives are too important to let them be ruled by (mostly contrived) political disagreements.”
If anything, those words seem more true today than they even did then. And I posit to you that the same applies for bitcoin.
Everyone has some sort of impression or opinion of bitcoin — and most of them are plain wrong. But there’s nothing people love more than a savior in white armor, riding in to dispel their errors about some thing they are freshly out of fucks for. Just like politics, nobody really cares.
Leave them alone. They will find bitcoin in their own time, just like all of us did.
This is a guest post by Joakim Book. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.

This is an opinion editorial by Federico Tenga, a long time contributor to Bitcoin projects with experience as start-up founder, consultant and educator.
The term “smart contracts” predates the invention of the blockchain and Bitcoin itself. Its first mention is in a 1994 article by Nick Szabo, who defined smart contracts as a “computerized transaction protocol that executes the terms of a contract.” While by this definition Bitcoin, thanks to its scripting language, supported smart contracts from the very first block, the term was popularized only later by Ethereum promoters, who twisted the original definition as “code that is redundantly executed by all nodes in a global consensus network”
While delegating code execution to a global consensus network has advantages (e.g. it is easy to deploy unowed contracts, such as the popularly automated market makers), this design has one major flaw: lack of scalability (and privacy). If every node in a network must redundantly run the same code, the amount of code that can actually be executed without excessively increasing the cost of running a node (and thus preserving decentralization) remains scarce, meaning that only a small number of contracts can be executed.
But what if we could design a system where the terms of the contract are executed and validated only by the parties involved, rather than by all members of the network? Let us imagine the example of a company that wants to issue shares. Instead of publishing the issuance contract publicly on a global ledger and using that ledger to track all future transfers of ownership, it could simply issue the shares privately and pass to the buyers the right to further transfer them. Then, the right to transfer ownership can be passed on to each new owner as if it were an amendment to the original issuance contract. In this way, each owner can independently verify that the shares he or she received are genuine by reading the original contract and validating that all the history of amendments that moved the shares conform to the rules set forth in the original contract.
This is actually nothing new, it is indeed the same mechanism that was used to transfer property before public registers became popular. In the U.K., for example, it was not compulsory to register a property when its ownership was transferred until the ‘90s. This means that still today over 15% of land in England and Wales is unregistered. If you are buying an unregistered property, instead of checking on a registry if the seller is the true owner, you would have to verify an unbroken chain of ownership going back at least 15 years (a period considered long enough to assume that the seller has sufficient title to the property). In doing so, you must ensure that any transfer of ownership has been carried out correctly and that any mortgages used for previous transactions have been paid off in full. This model has the advantage of improved privacy over ownership, and you do not have to rely on the maintainer of the public land register. On the other hand, it makes the verification of the seller’s ownership much more complicated for the buyer.

Source: Title deed of unregistered real estate propriety
How can the transfer of unregistered properties be improved? First of all, by making it a digitized process. If there is code that can be run by a computer to verify that all the history of ownership transfers is in compliance with the original contract rules, buying and selling becomes much faster and cheaper.
Secondly, to avoid the risk of the seller double-spending their asset, a system of proof of publication must be implemented. For example, we could implement a rule that every transfer of ownership must be committed on a predefined spot of a well-known newspaper (e.g. put the hash of the transfer of ownership in the upper-right corner of the first page of the New York Times). Since you cannot place the hash of a transfer in the same place twice, this prevents double-spending attempts. However, using a famous newspaper for this purpose has some disadvantages:
- You have to buy a lot of newspapers for the verification process. Not very practical.
- Each contract needs its own space in the newspaper. Not very scalable.
- The newspaper editor can easily censor or, even worse, simulate double-spending by putting a random hash in your slot, making any potential buyer of your asset think it has been sold before, and discouraging them from buying it. Not very trustless.
For these reasons, a better place to post proof of ownership transfers needs to be found. And what better option than the Bitcoin blockchain, an already established trusted public ledger with strong incentives to keep it censorship-resistant and decentralized?
If we use Bitcoin, we should not specify a fixed place in the block where the commitment to transfer ownership must occur (e.g. in the first transaction) because, just like with the editor of the New York Times, the miner could mess with it. A better approach is to place the commitment in a predefined Bitcoin transaction, more specifically in a transaction that originates from an unspent transaction output (UTXO) to which the ownership of the asset to be issued is linked. The link between an asset and a bitcoin UTXO can occur either in the contract that issues the asset or in a subsequent transfer of ownership, each time making the target UTXO the controller of the transferred asset. In this way, we have clearly defined where the obligation to transfer ownership should be (i.e in the Bitcoin transaction originating from a particular UTXO). Anyone running a Bitcoin node can independently verify the commitments and neither the miners nor any other entity are able to censor or interfere with the asset transfer in any way.
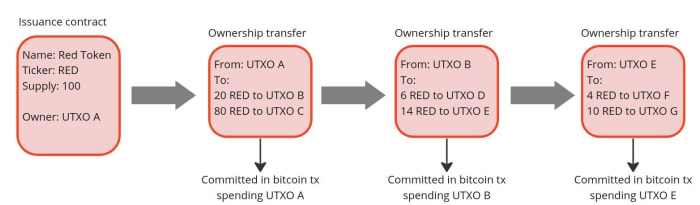
Since on the Bitcoin blockchain we only publish a commitment of an ownership transfer, not the content of the transfer itself, the seller needs a dedicated communication channel to provide the buyer with all the proofs that the ownership transfer is valid. This could be done in a number of ways, potentially even by printing out the proofs and shipping them with a carrier pigeon, which, while a bit impractical, would still do the job. But the best option to avoid the censorship and privacy violations is establish a direct peer-to-peer encrypted communication, which compared to the pigeons also has the advantage of being easy to integrate with a software to verify the proofs received from the counterparty.
This model just described for client-side validated contracts and ownership transfers is exactly what has been implemented with the RGB protocol. With RGB, it is possible to create a contract that defines rights, assigns them to one or more existing bitcoin UTXO and specifies how their ownership can be transferred. The contract can be created starting from a template, called a “schema,” in which the creator of the contract only adjusts the parameters and ownership rights, as is done with traditional legal contracts. Currently, there are two types of schemas in RGB: one for issuing fungible tokens (RGB20) and a second for issuing collectibles (RGB21), but in the future, more schemas can be developed by anyone in a permissionless fashion without requiring changes at the protocol level.
To use a more practical example, an issuer of fungible assets (e.g. company shares, stablecoins, etc.) can use the RGB20 schema template and create a contract defining how many tokens it will issue, the name of the asset and some additional metadata associated with it. It can then define which bitcoin UTXO has the right to transfer ownership of the created tokens and assign other rights to other UTXOs, such as the right to make a secondary issuance or to renominate the asset. Each client receiving tokens created by this contract will be able to verify the content of the Genesis contract and validate that any transfer of ownership in the history of the token received has complied with the rules set out therein.
So what can we do with RGB in practice today? First and foremost, it enables the issuance and the transfer of tokenized assets with better scalability and privacy compared to any existing alternative. On the privacy side, RGB benefits from the fact that all transfer-related data is kept client-side, so a blockchain observer cannot extract any information about the user’s financial activities (it is not even possible to distinguish a bitcoin transaction containing an RGB commitment from a regular one), moreover, the receiver shares with the sender only blinded UTXO (i. e. the hash of the concatenation between the UTXO in which she wish to receive the assets and a random number) instead of the UTXO itself, so it is not possible for the payer to monitor future activities of the receiver. To further increase the privacy of users, RGB also adopts the bulletproof cryptographic mechanism to hide the amounts in the history of asset transfers, so that even future owners of assets have an obfuscated view of the financial behavior of previous holders.
In terms of scalability, RGB offers some advantages as well. First of all, most of the data is kept off-chain, as the blockchain is only used as a commitment layer, reducing the fees that need to be paid and meaning that each client only validates the transfers it is interested in instead of all the activity of a global network. Since an RGB transfer still requires a Bitcoin transaction, the fee saving may seem minimal, but when you start introducing transaction batching they can quickly become massive. Indeed, it is possible to transfer all the tokens (or, more generally, “rights”) associated with a UTXO towards an arbitrary amount of recipients with a single commitment in a single bitcoin transaction. Let’s assume you are a service provider making payouts to several users at once. With RGB, you can commit in a single Bitcoin transaction thousands of transfers to thousands of users requesting different types of assets, making the marginal cost of each single payout absolutely negligible.
Another fee-saving mechanism for issuers of low value assets is that in RGB the issuance of an asset does not require paying fees. This happens because the creation of an issuance contract does not need to be committed on the blockchain. A contract simply defines to which already existing UTXO the newly issued assets will be allocated to. So if you are an artist interested in creating collectible tokens, you can issue as many as you want for free and then only pay the bitcoin transaction fee when a buyer shows up and requests the token to be assigned to their UTXO.
Furthermore, because RGB is built on top of bitcoin transactions, it is also compatible with the Lightning Network. While it is not yet implemented at the time of writing, it will be possible to create asset-specific Lightning channels and route payments through them, similar to how it works with normal Lightning transactions.
Conclusion
RGB is a groundbreaking innovation that opens up to new use cases using a completely new paradigm, but which tools are available to use it? If you want to experiment with the core of the technology itself, you should directly try out the RGB node. If you want to build applications on top of RGB without having to deep dive into the complexity of the protocol, you can use the rgb-lib library, which provides a simple interface for developers. If you just want to try to issue and transfer assets, you can play with Iris Wallet for Android, whose code is also open source on GitHub. If you just want to learn more about RGB you can check out this list of resources.
This is a guest post by Federico Tenga. Opinions expressed are entirely their own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.